
Technical documentation
发布日期:2023-04-06 浏览次数:3922 来源:WOLFLAB
HCIE Datacom培训LAB实验笔记(原数通RS)-虚拟防火墙
关注WOLFLAB网络技术实验室,HCIE Datacom培训阶段提供1v1技术辅导,考试资讯联系WOLFLAB!
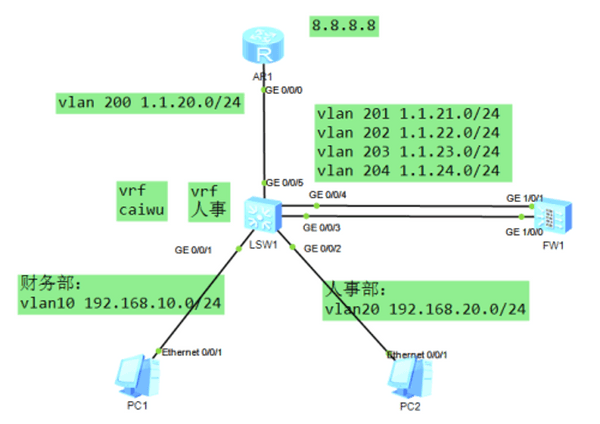
虚拟防火墙:就是防火墙的vpn-instance
实验:
需求一:
①两个部门都可以经过FW访问internet
②部门之间不能互相访问
[SW1]dis current-configuration
#
sysname SW1
#
vlan batch 10 20 200 to 204
#
ip vpn-instance caiwu
ipv4-family
route-distinguisher 1:1
#
ip vpn-instance renshi
ipv4-family
route-distinguisher 1:2
#
interface Vlanif10
ip binding vpn-instance caiwu
ip address 192.168.10.254 255.255.255.0
#
interface Vlanif20
ip binding vpn-instance renshi
ip address 192.168.20.254 255.255.255.0
#
interface Vlanif200
ip address 1.1.20.1 255.255.255.0
#
interface Vlanif201
ip address 1.1.21.1 255.255.255.0
#
interface Vlanif202
ip address 1.1.22.1 255.255.255.0
#
interface Vlanif203
ip binding vpn-instance caiwu
ip address 1.1.23.1 255.255.255.0
#
interface Vlanif204
ip binding vpn-instance renshi
ip address 1.1.24.1 255.255.255.0
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 201 to 204
mode lacp-static
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/3
eth-trunk 1
#
interface GigabitEthernet0/0/4
eth-trunk 1
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 200
#
ip route-static 0.0.0.0 0.0.0.0 1.1.20.2
ip route-static 192.168.10.0 255.255.255.0 1.1.21.2
ip route-static 192.168.20.0 255.255.255.0 1.1.22.2
ip route-static vpn-instance caiwu 0.0.0.0 0.0.0.0 1.1.23.2
ip route-static vpn-instance renshi 0.0.0.0 0.0.0.0 1.1.24.2
[USG6000V1]
#
sysname USG6000V1
#
vlan batch 201 to 204
#
vsys enable //开启虚拟防火墙的功能
#
vsys name caiwu 1 //创建虚拟防火墙财务
assign vlan 201 //将接口vlan201划入到该虚墙
assign vlan 203
#
vsys name renshi 2
assign vlan 202
assign vlan 204
#
interface Vlanif201
ip binding vpn-instance caiwu
ip address 1.1.21.2 255.255.255.0
#
interface Vlanif202
ip binding vpn-instance renshi
ip address 1.1.22.2 255.255.255.0
#
interface Vlanif203
ip binding vpn-instance caiwu
ip address 1.1.23.2 255.255.255.0
#
interface Vlanif204
ip binding vpn-instance renshi
ip address 1.1.24.2 255.255.255.0
#
interface Eth-Trunk1
portswitch
port link-type trunk
port trunk allow-pass vlan 201 to 204
mode lacp-static
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
interface Virtual-if0 //虚拟接口是自动生成的,public是0,按照创建虚墙的顺序依次是1、2
#
interface Virtual-if1
#
interface Virtual-if2
#
switch vsys caiwu //进入到虚墙caiwu下
#
interface Vlanif201
ip binding vpn-instance caiwu
ip address 1.1.21.2 255.255.255.0
#
interface Vlanif203
ip binding vpn-instance caiwu
ip address 1.1.23.2 255.255.255.0
#
interface Virtual-if1
#
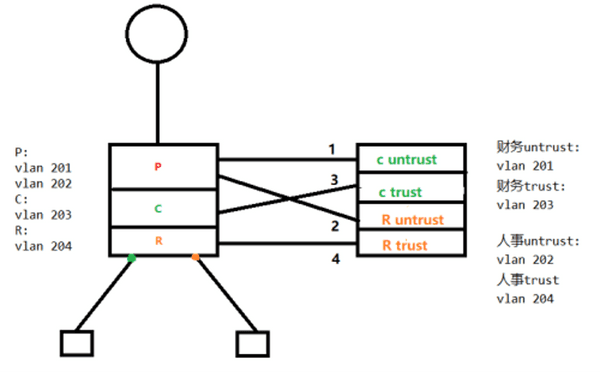
firewall zone trust //将接口划入到虚墙的安全区域
set priority 85
add interface Vlanif203
#
firewall zone untrust
set priority 5
add interface Vlanif201
#
security-policy //创建安全策略
rule name caiwu_to_internet
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
#
ip route-static 0.0.0.0 0.0.0.0 1.1.21.1
ip route-static 192.168.10.0 255.255.255.0 1.1.23.1
#
return
#
switch vsys renshi
#
interface Vlanif202
ip binding vpn-instance renshi
ip address 1.1.22.2 255.255.255.0
#
interface Vlanif204
ip binding vpn-instance renshi
ip address 1.1.24.2 255.255.255.0
#
interface Virtual-if2
#
firewall zone trust
set priority 85
add interface Vlanif204
#
firewall zone untrust
set priority 5
add interface Vlanif202
#
security-policy
rule name renshi_to_internet
source-zone trust
destination-zone untrust
source-address 192.168.20.0 mask 255.255.255.0
action permit
#
ip route-static 0.0.0.0 0.0.0.0 1.1.22.1
ip route-static 192.168.20.0 255.255.255.0 1.1.24.1
#
return
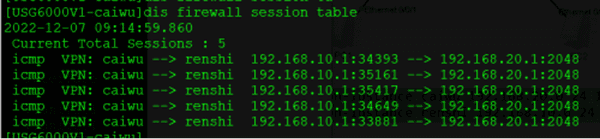
HCIE Datacom培训实战练习需求二:
①两个部门都可以经过访问internet
②部门之间可以互相访问但是要经过FW
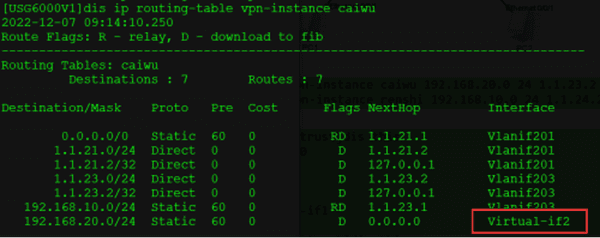
[SW1]ip route-static vpn-instance caiwu 192.168.20.0 24 1.1.23.2
[SW1]ip route-static vpn-instance renshi 192.168.10.0 24 1.1.24.2
[USG6000V1-caiwu-zone-trust]dis this
2022-12-07 09:08:59.260
#
firewall zone trust
set priority 85
add interface Virtual-if1
[USG6000V1-renshi-zone-trust]dis this
2022-12-07 09:09:24.790
#
firewall zone trust
set priority 85
add interface Virtual-if2
add interface Vlanif204
[USG6000V1]ip route-static vpn-instance caiwu 192.168.20.0 24 vpn-instance renshi
[USG6000V1]ip route-static vpn-instance renshi 192.168.10.0 24 vpn-instance caiwu
HCIE Datacom培训咨询联系WOLFLAB网络技术实验室
欢迎关注WOLFLAB(沃尔夫)网络实验室,华为认证HCIE认证讲师:崔志鹏
了解HCIE Datacom相关技术学习,可联系WOLFLAB(沃尔夫)实验室!