
Technical documentation
发布日期:2023-06-26 浏览次数:5113 来源:崔志鹏
华为认证HCIE Datacom培训SRV6 BE L3 VPN实验配置详解

WOLFLAB官方微信:17316362402,华为认证HCIE Datacom培训课程试听预约WOLFLAB,HCIA、HCIP、HCIE培训学习考试都在循环开班,找网站客服获取基础课程免费资料一套!
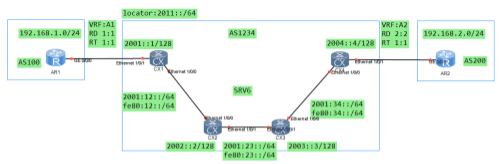
实验:实现192.168.1.0/24能够访问192.168.2.0/24
HCIE Datacom培训课程
第一步:ISP配置IPV6地址
CX1/CX2/CX3/CX4:
undo dcn
[CX1-Ethernet1/0/0]dis this
#
interface Ethernet1/0/0
ipv6 enable
ipv6 address 2001:12::1/64
ipv6 address FE80:12::1 link-local
#
interface LoopBack0
ipv6 enable
ipv6 address 2001::1/128
第二步:配置底层IGP协议
[CX1-isis-1]dis this
#
isis 1
is-level level-2
cost-style wide
network-entity 49.0001.0000.0000.0001.00
#
ipv6 enable topology ipv6
#
interface Ethernet1/0/0
isis ipv6 enable 1
#
interface LoopBack0
isis ipv6 enable 1
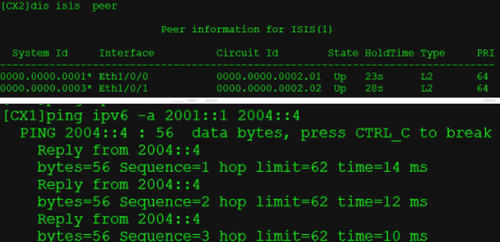
验证:
第三步:配置PE和CE接入协议
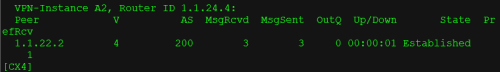
第四步:CX1和CX4建立VPNV4邻居关系
[CX1-bgp]dis this
#
bgp 1234
router-id 1.1.1.1 //router-id必须配置否则邻居无法建立
undo default ipv4-unicast
peer 2004::4 as-number 1234
peer 2004::4 connect-interface LoopBack0
#
ipv4-family vpnv4
policy vpn-target
peer 2004::4 enable
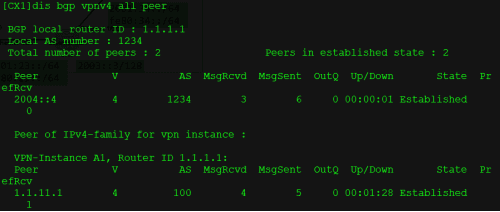
第五步:PE设备上配置SRV6-BE,P设备无需配置
CX1:
segment-routing ipv6
encapsulation source-address 2001::1 //相当于隧道的源地址
locator wolf ipv6-prefix 2011:: 64 static 64 //SRV6 SID的地址池
#
isis 1
segment-routing ipv6 locator wolf auto-sid-disable //将locator对应网段的路由发布出去,同时关闭自动配置opcode,采用手动配置方式
CX4:
segment-routing ipv6
encapsulation source-address 2004::4
locator wolf ipv6-prefix 2044:: 64 static 64
#
isis 1
segment-routing ipv6 locator wolf auto-sid-disable
验证:四台设备都可以学到CX1和CX4的locator网段的路由,因为是通过ISIS发布的
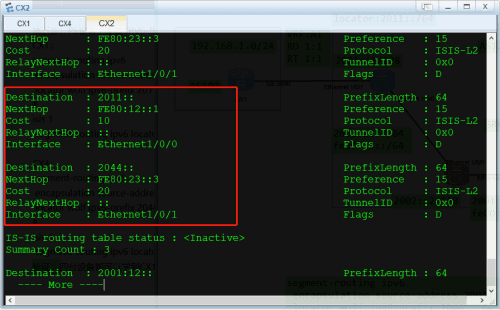
第六步:配置封装IPV4报文的IPV6头部的目的地址(私网标签)
CX1:
segment-routing ipv6
locator wolf
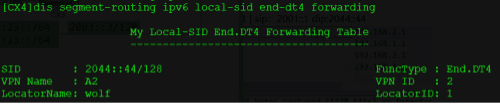
opcode ::11 end-dt4 vpn-instance A1 //配置针对VRF A1下的路由分配2011::11SRV6 SID(私网标签)
CX4:
segment-routing ipv6
locator wolf
opcode ::44 end-dt4 vpn-instance A2
CX1:
bgp 1234
#
ipv4-family vpnv4
peer 2004::4 enable
peer 2004::4 prefix-sid //给CX4通告SRV6 SID(私网标签)
#
ipv4-family vpn-instance A1
segment-routing ipv6 locator wolf auto-sid-disable //针对VRF A1下的路由使用locator wolf,end和end.x由IGP自动分配,关闭自动分配;
segment-routing ipv6 best-effort //启用SRV6-BE
CX4:
bgp 1234
#
ipv4-family vpnv4
peer 2001::1 enable
peer 2001::1 prefix-sid
#
ipv4-family vpn-instance A2
segment-routing ipv6 locator wolf auto-sid-disable
segment-routing ipv6 best-effort
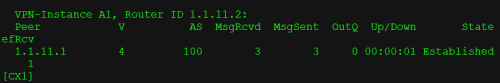
验证:CX4再给CX1发送192.168.2.0的路由会携带prefix-sid 2044:44
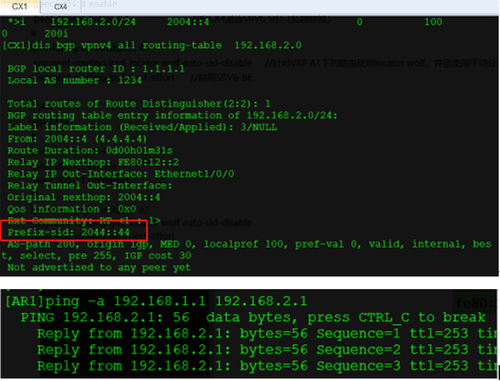
路由传递:
①AR2将自己的192.168.2.0/24的路由通过BGP邻居传递给CX4;
②CX4为192.168.2.0/24的路由添加RD 1:1 RT 1:1 PREFIX-SID 2044::44,通过VPNV4邻居传递给CX1;
③CX1收到该路由后根据RT值导入进自己的VRF A1的路由表中;
④CX1再将该路由通过BGP邻居关系传递给AR1;
流量分析:
①AR1-CX1:icmp request | sip:192.168.1.1 dip:192.168.2.1
②CX1收到后,根据报文的目的地址查路由,匹配192.168.2.0/24的路由,将该IPV4的数据包挂一个IPV6的外层头部,sip:就是segment-routing ipv6配置的地址,dip:CX4传递192.168.2.0路由携带的PREFIX-SID;
icmp request | sip:192.168.1.1 dip:192.168.2.1 | sip:2001::1 dip:2044::44
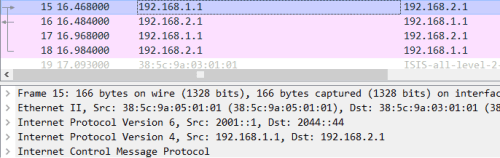
③CX2根据最外层的IPV6头部查自己的路由表做报文的转发,报文不动发送给CX3:
icmp request | sip:192.168.1.1 dip:192.168.2.1 | sip:2001::1 dip:2044::44
④CX3根据最外层的IPV6头部查自己的路由表做报文的转发,报文不动发送给CX4:
⑤CX4根据最外层头部的DIP,查自己的对应的VRF表象,将报文发送给AR2;
华为HCIE Datacom培训课程联系WOLFLAB预约免费试听
WOLFLAB实验室HCIE讲师:崔志鹏
WOLFLAB网络技术实验室-华为授权机构
WOLFLAB官方微信:17316362402
WOLFLAB官方QQ:2569790740