
Technical documentation
发布日期:2023-03-29 浏览次数:3745 来源:WOLFLAB
HCIE Datacom培训考试-学习防火墙部署方式直连式和旁挂式
WOLFLAB官方微信:17316362402,关注WOLFLAB网络技术实验室,了解HCIE Datacom培训相关课程!
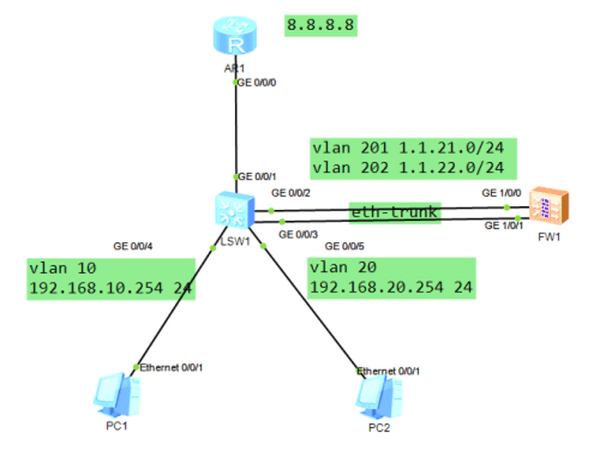
第一种:直连式,所有流量都要过防火墙不方便管理

第二种:旁挂式,流量是否过防火墙或者哪种流量需要过防火墙由管理员决定

方法一:VRF
[SW1]dis cur
[SW1]dis current-configuration
sysname SW1
#
vlan batch 10 20 30 201 to 202
#
ip vpn-instance WOLF
ipv4-family
route-distinguisher 1:1
#
interface Vlanif10
ip binding vpn-instance WOLF
ip address 192.168.10.254 255.255.255.0
#
interface Vlanif20
ip binding vpn-instance WOLF
ip address 192.168.20.254 255.255.255.0
#
interface Vlanif30
ip address 1.1.12.2 255.255.255.0
#
interface Vlanif201
ip binding vpn-instance WOLF
ip address 1.1.21.1 255.255.255.0
#
interface Vlanif202
ip address 1.1.22.1 255.255.255.0
#
interface Eth-Trunk1
port link-type trunk
port trunk allow-pass vlan 201 to 202
mode lacp-static
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 30
#
interface GigabitEthernet0/0/2
eth-trunk 1
#
interface GigabitEthernet0/0/3
eth-trunk 1
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 20
#
ip route-static 0.0.0.0 0.0.0.0 1.1.12.1
ip route-static 192.168.10.0 255.255.255.0 1.1.22.2
ip route-static 192.168.20.0 255.255.255.0 1.1.22.2
ip route-static vpn-instance WOLF 0.0.0.0 0.0.0.0 1.1.21.2
#
return
[USG6000V1]dis current-configuration
sysname USG6000V1
#
vlan batch 201 to 202
#
interface Vlanif201
ip address 1.1.21.2 255.255.255.0
#
interface Vlanif202
ip address 1.1.22.2 255.255.255.0
#
interface Eth-Trunk1
portswitch
port link-type trunk
port trunk allow-pass vlan 201 to 202
mode lacp-static
#
interface GigabitEthernet1/0/0
undo shutdown
eth-trunk 1
#
interface GigabitEthernet1/0/1
undo shutdown
eth-trunk 1
#
firewall zone trust
add interface Vlanif201
#
firewall zone untrust
add interface Vlanif202
#
ip route-static 0.0.0.0 0.0.0.0 1.1.22.1
ip route-static 192.168.10.0 255.255.255.0 1.1.21.1
ip route-static 192.168.20.0 255.255.255.0 1.1.21.1
#
security-policy
rule name internet
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0 //只允许192.168.10.0/24网段主机访问internet
action permit
#
return
问题一:假设SW1上配置的静态路由如下
ip route-static vpn-instance WOLF 0.0.0.0 0.0.0.0 1.1.12.1 public
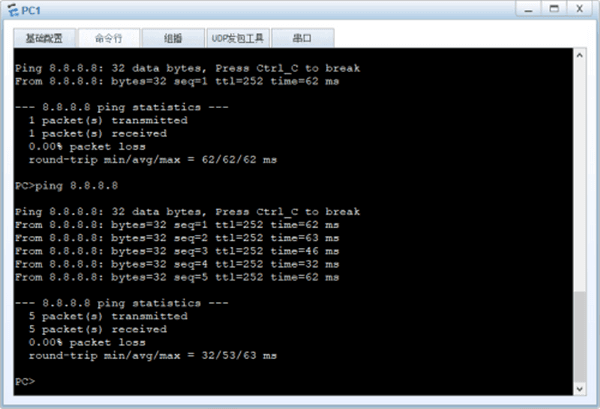
此时PC1访问internet直接去回来走防火墙,出现非对称路由,此时PC1能否ping通8.8.8.8?
不行,因为FW收到的reply报文是非首包,没有写策略。
[USG6000V1-policy-security]dis this
2022-12-05 09:01:00.640
#
security-policy
rule name internet
source-zone trust
destination-zone untrust
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name return
source-zone untrust
destination-zone trust
destination-address 192.168.10.0 mask 255.255.255.0
action permit
问题二:写完策略能否ping通?
不行,因为防火墙是状态检测防火墙,收到reply报文,认为是攻击报文,需要将防火墙的状态检测机制关闭掉
undo firewall session link-state check
方法二:策略路由
SW1:
policy-based-route out permit node 10
if-match acl 3000
apply ip-address next-hop 1.1.21.2
acl number 3000
rule 5 permit ip source 192.168.10.0 0.0.0.255
ip local policy-based-route out
注意:模拟器只能采用本地调用,所以只能让交换机以自己的192168.10.254为源进行测试;
状态检测机制:
①对于TCP报文
开启状态检测机制时,首包(SYN报文)建立会话表项。对除SYN报文外的其他报文,如果没有对应会话表项(设备没有收到SYN报文或者会话表项已老化)则予以丢弃,也不会建立会话表项。
关闭状态检测机制时,任何格式的报文在没有对应会话表项的情况下,只要通过各项安全机制的检查,都可以为其建立会话表项。
②对于UDP报文
UDP是基于无连接的通信,任何UDP格式的报文在没有对应会话表项的情况下,只要通过各项安全机制的检查,都可以为其建立会话表项。
③对于ICMP报文
开启状态检测机制时,没有对应会话的ICMP应答报文将被丢弃。
关闭状态检测机制时,没有对应会话的应答报文以首包形式处理。
欢迎关注WOLFLAB(沃尔夫)网络实验室
HCIE Datacom培训循环开班,点击这里预约
WOLFLAB官方微信:17316362402
WOLFLAB官方QQ:2569790740