
News
发布日期:2022-07-22 浏览次数:6140 来源:杨广成
思科CCIE培训课程笔记-IKEv2解决方案FlexVPN(2)
WOLFLAB官方微信:17316362402,联系客服获取免费学习资料,CCIE培训课程循环开班中。
FlexVPN当中,一种新的Server-Client模式,包括Remote-access , Hub-Spoke,将被用于统一DMVPN和EZVPN,好处是“公有”,X-AUTH变成了EAP,这样客户端无需再使用Cisco VPN Client,而是直接用Windows 7都可以支持。
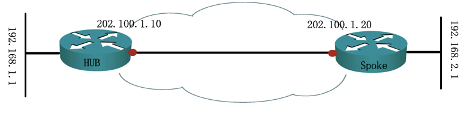
一、底层配置
R1
int lo 0
ip add 192.168.1.1 255.255.255.0
int e0/0
ip add 202.100.1.10 255.255.255.0
no shut
R2
int lo 0
ip add 192.168.2.1 255.255.255.0
int e0/0
ip add 202.100.1.20 255.255.255.0
no shut
二、Hub端配置
R1
aaa new-model
aaa authentication login NOAU line none
line con 0
login authentication NOAU
line aux 0
login authentication NOAU
aaa authorization network remote local
ip local pool P 192.168.100.1 192.168.100.100
crypto ikev2 authorization policy HUB-P //类似EZVPN服务端的Group配置
pool P
route set interface // 除了route set interface 还可以做route set access-list XXX
//解释:
(1)route set interface表示将本端virtual-template/tunnel接口的IP地址路由推给对端安装为静态路由(出接口为virtual-access或Tunnel,下一跳0.0.0.0)
意义在于,virtual-template接口通常会ip unnumbered借用一个本地接口地址,而当借用的是loopback地址时,对端必然无路由。
当在virtual-access/Tunnel接口运行一个单播的动态路由协议时,neighbor指对端地址,单播无路由,就无法建立路由协议邻居关系了。
(2)route set access-list XXX 搭配一个ACL,将ACL描述的路由推送给对端安装为静态路由(出接口为virtual-access或Tunnel,下一跳0.0.0.0), 注意只能是标准列表, 扩展列表不生效。
CCIE培训课程试听可联系WOLFLAB网站客服
crypto ikev2 keyring KEY
peer SPOKES
address 0.0.0.0 0.0.0.0
pre-shared-key cisco123
crypto ipsec transform-set TS esp-3des esp-sha-hmac
crypto ikev2 profile V2-P
match identity remote address 0.0.0.0
authentication remote pre-share
authentication local pre-share
keyring local KEY
aaa authorization group psk list remote HUB-P //本地拿授权(remote定义了local),授权在HUB-P中
virtual-template 1
crypto ipsec profile IPSEC-P
set transform-set TS
set ikev2-profile V2-P
int virtual-template 1 type tunnel
ip unnumbered lo 0 //绝不可以和加密点接口相同,否则对方可能会从物理口和tunnel口学到相同的路由(route set interface情况下)
tunnel source e0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSEC-P
三、SPOKE端配置
R2
aaa new-model
aaa authentication login NOAU line none
line con 0
login authentication NOAU
line aux 0
login authentication NOAU
aaa authorization network remote local
crypto ikev2 authorization policy SPOKE-P
route set interface //推送自己tunnel口获取到的地址对应路由给server
crypto ikev2 keyring KEY
peer HUB
address 202.100.1.10
pre-shared-key cisco123
crypto ikev2 profile V2-P
match identity remote address 202.100.1.10 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local KEY
aaa authorization group override psk list remote SPOKE-P //override参数表示组授权优先于用户授权,不打这个参数则是用户授权优于组授权。这里因为没有做用户授权,所以无所谓。
crypto ipsec transform-set TS esp-3des esp-sha-hmac
crypto ipsec profile IPSEC-P
set transform-set TS
set ikev2-profile V2-P
interface Tunnel0
ip address negotiated
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination dynamic //考虑到有双HUB或者backup server的情况下,便于用一套配置连多个HUB(server)
tunnel protection ipsec profile IPSEC-P
crypto ikev2 client flexvpn FLEX
peer 1 202.100.1.10
connect manual
client connect Tunnel0
测试:
cryp ikev2 client flexvpn connect FLEX //手动拨号
R2 ping 192.168.1.1 sour 192.168.2.1 不通, 因为R2没有给R1推送 192.168.2.0的路由
ip access-list standard ACL
permit 192.168.2.0 0.0.0.255
crypto ikev2 authorization policy SPOKE-P
route set access-list ACL
断线重拨
R1 show ip route 可以看到192.168.2.0/24的路由了 , ping可以通。
CCIE培训课程实验二:再加入一台R3,做第二台Spoke
R3
int lo 0
ip add 192.168.3.1 255.255.255.0
int e0/0
ip add 202.100.1.30 255.255.255.0
no shutdown
aaa new-model
aaa authentication login NOAU line none
line con 0
login authentication NOAU
line aux 0
login authentication NOAU
aaa authorization network remote local
ip access-list standard ACL
permit 192.168.3.0 0.0.0.255
crypto ikev2 authorization policy SPOKE-P
route set interface
route set access-list ACL
crypto ikev2 keyring KEY
peer HUB
address 202.100.1.10
pre-shared-key cisco123
crypto ikev2 profile V2-P
match identity remote address 202.100.1.10 255.255.255.255
authentication remote pre-share
authentication local pre-share
keyring local KEY
aaa authorization group override psk list remote SPOKE-P
crypto ipsec transform-set TS esp-3des esp-sha-hmac
crypto ipsec profile IPSEC-P
set transform-set TS
set ikev2-profile V2-P
interface Tunnel0
ip address negotiated
tunnel source Ethernet0/0
tunnel mode ipsec ipv4
tunnel destination dynamic
tunnel protection ipsec profile IPSEC-P
crypto ikev2 client flexvpn FLEX
peer 1 202.100.1.10
connect manual
client connect Tunnel0
测试
cryp ikev2 client flexvpn connect FLEX //手动拨号
会看到R1多产生了一个Virtual-Access接口
R1 show ip route
S 192.168.2.0/24 [2/0] via 0.0.0.0, Virtual-Access1
S 192.168.3.0/24 [2/0] via 0.0.0.0, Virtual-Access2
问题是:
光靠route set注入的静态路由, R2和R3两个SPOKE之间是无法互访的(SPOKE没有SPOKE的路由)
R3 show ip route
192.168.1.0/32 is subnetted, 1 subnets
S 192.168.1.1 [2/0] via 0.0.0.0, Tunnel0
192.168.3.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.3.0/24 is directly connected, Loopback0
L 192.168.3.1/32 is directly connected, Loopback0
192.168.100.0/32 is subnetted, 1 subnets
C 192.168.100.5 is directly connected, Tunnel0
202.100.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 202.100.1.0/24 is directly connected, Ethernet0/0
L 202.100.1.30/32 is directly connected, Ethernet0/0
因此可以运行动态路由协议:
R1
int lo 0
ip ospf 1 area 0
int virtual-template 1
ip ospf 1 area 0
R2
int lo 0
ip ospf 1 area 0
int tunnel 0
ip ospf 1 area 0
R3
int lo 0
ip ospf 1 area 0
int tunnel 0
ip ospf 1 area 0
R1#sh ip os nei
Neighbor ID Pri State Dead Time Address Interface
192.168.2.1 0 FULL/ - 00:00:33 192.168.100.3 Virtual-Access1
192.168.3.1 0 FULL/ - 00:00:31 192.168.100.5 Virtual-Access2
R2#show ip route
192.168.1.0/32 is subnetted, 1 subnets
S 192.168.1.1 [2/0] via 0.0.0.0, Tunnel0
192.168.2.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.2.0/24 is directly connected, Loopback0
L 192.168.2.1/32 is directly connected, Loopback0
192.168.3.0/32 is subnetted, 1 subnets
O 192.168.3.1 [110/1002] via 192.168.1.1, 00:08:44, Tunnel0
192.168.100.0/32 is subnetted, 2 subnets
C 192.168.100.3 is directly connected, Tunnel0
O 192.168.100.5 [110/2001] via 192.168.1.1, 00:08:44, Tunnel0
202.100.1.0/24 is variably subnetted, 2 subnets, 2 masks
C 202.100.1.0/24 is directly connected, Ethernet0/0
L 202.100.1.20/32 is directly connected, Ethernet0/0
R2#ping 192.168.3.1 source 192.168.2.1
!!!!! 能通,但是是通过R1周转的。 如果希望R2能够直接向R3建立隧道,流量直达怎么做?
——问题关键在于:
(1)要设法让SPOKE知道想要访问的其他SPOKE公网IP
(2)要让SPOKE可以有动态发起Tunnel到其他SPOKE的能力
CCIE培训课程实验三: SPOKE--TO---SPOKE
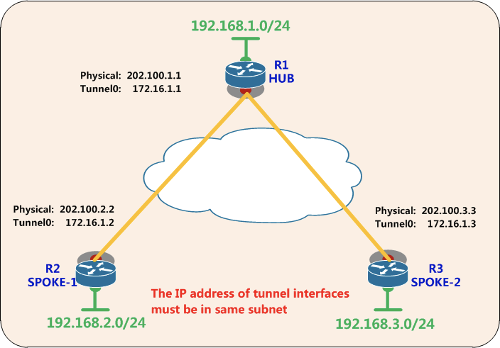
在之前的实验基础上:
(1)Spoke端身份认证key的适用范围需要扩大为 0.0.0.0
(2)tunnel模式不能使用VTI,只能是GRE
(3)NHRP
(1)Spoke端身份认证key的适用范围需要扩大为 0.0.0.0
R2/R3
crypto ikev2 keyring KEY
peer SPOKES
address 0.0.0.0 0.0.0.0
pre-shared-key cisco123
crypto ikev2 profile V2-P
match identity remote address 0.0.0.0
(2)tunnel模式不能使用VTI,只能是GRE; Spoke端tunnel需明确指向Hub端
R1
int virtual-template 1
tunnel mode gre ip //改回默认模式 ,也可以打no tunnel mode恢复默认的GRE模式
R2/R3
crypto ikev2 client flexvpn FLEX
no client connect Tunnel0 //必须摘掉这个调用,否则改不了tunnel模式
//其实已经不需要crypto ikev2 client flexvpn FLEX,因为tunnel改模式后,tunnel destination地址是明确的,不需要参考client配置中的peer地址建立了。所以直接删除后,tunnel口的路由协议流量,nhrp流量,都会触发VPN的拨号。
int tunnel 0
tunnel mode gre ip
no tunnel destination dynamic
tunnel destination 202.100.1.10
(3)开启NHRP
R1
int virtual-template1
ip nhrp network-id 123
ip nhrp redirect
R2/R3
int tunnel 0
ip nhrp network-id 123
ip nhrp shortcut virtual-template 1
int virtual-template 1 type tunnel
ip unnumbered tunnel 0
ip nhrp network-id 123
ip nhrp shortcut
ip ospf 1 area 0
tunnel source e0/0
tunnel protection ipsec profile IPSEC-P
测试:
R2#sh cry sess //一开始R2只有一个VPN会话
Crypto session current status
Interface: Tunnel0
Session status: UP-ACTIVE
Peer: 202.100.1.10 port 500
IKEv2 SA: local 202.100.1.20/500 remote 202.100.1.10/500 Active
IPSEC FLOW: permit 47 host 202.100.1.20 host 202.100.1.10
Active SAs: 2, origin: crypto map
R2#ping 192.168.3.1 sour 192.168.2.1 repeat 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 192.168.3.1, timeout is 2 seconds:
Packet sent with a source address of 192.168.2.1
.!!!!!!!!!
Success rate is 90 percent (9/10), round-trip min/avg/max = 6/14/34 ms
*Aug 9 10:39:52.182: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up //动态创建了去往R3的接口
R2#sh cry sess //R2有两个VPN会话了
Crypto session current status
Interface: Tunnel0
Session status: UP-ACTIVE
Peer: 202.100.1.10 port 500
IKEv2 SA: local 202.100.1.20/500 remote 202.100.1.10/500 Active
IPSEC FLOW: permit 47 host 202.100.1.20 host 202.100.1.10
Active SAs: 2, origin: crypto map
Interface: Virtual-Access1
Session status: UP-ACTIVE
Peer: 202.100.1.30 port 500
IKEv2 SA: local 202.100.1.20/500 remote 202.100.1.30/500 Active
IPSEC FLOW: permit 47 host 202.100.1.20 host 202.100.1.30
Active SAs: 2, origin: crypto map
R2#sh ip route
H 192.168.3.0/24 [250/1] via 192.168.100.2, 00:00:16
R2#sh ip nhrp
192.168.3.0/24 via 192.168.100.2
Tunnel0 created 00:00:48, expire 01:59:29
Type: dynamic, Flags: router rib
NBMA address: 202.100.1.30
CCIE培训课程试听联系WOLFLAB网站客服,安排免费试听。