
News
发布日期:2023-07-03 浏览次数:3471 来源:崔志鹏
华为认证HCIE培训(Datacom)课程-手动IPSEC VPN详细笔记

WOLFLAB官方微信:17316362402,华为认证HCIE培训(Datacom)课程咨询可联系WOLFLAB资讯详情!
华为认证HCIE培训-手动IPSEC VPN(ESP):
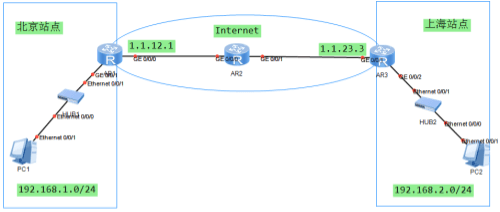
第一步:匹配感兴趣流(需要保护的数据)
[AR1-acl-adv-3000]dis this
[V200R003C00]
#
acl number 3000
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
[AR3-acl-adv-3000]dis this
[V200R003C00]
#
acl number 3000
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
第二步:创建安全提议(合同的内容)
AR1/AR3:
ipsec proposal wolf
[AR1]dis ipsec proposal //默认参数
Number of proposals: 1
IPSec proposal name: wolf
Encapsulation mode: Tunnel //传输模式隧道
Transform : esp-new //采用ESP封装
ESP protocol : Authentication MD5-HMAC-96 //认证算法MD5
Encryption DES //加密算法DES
第三步:创建安全策略
[AR1-ipsec-policy-manual-wolf-10]dis this
[V200R003C00]
#
ipsec policy wolf 10 manual
security acl 3000
proposal wolf
tunnel local 1.1.12.1
tunnel remote 1.1.23.3
sa spi inbound esp 1234 //AR1的 inbound 是AR3的 outbound
sa string-key inbound esp simple huawei
sa spi outbound esp 4321 //AR1的 outbound 是AR3的 inbound
sa string-key outbound esp simple huawei
[AR3-ipsec-policy-manual-wolf-10]dis this
[V200R003C00]
#
ipsec policy wolf 10 manual
security acl 3000
proposal wolf
tunnel local 1.1.23.3
tunnel remote 1.1.12.1
sa spi inbound esp 4321
sa string-key inbound esp simple huawei
sa spi outbound esp 1234
sa string-key outbound esp simple huawei
第四步:接口下调用安全策略
interface GigabitEthernetX/X/X
ipsec policy wolf
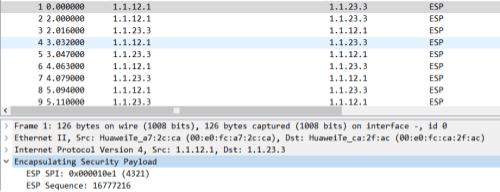
验证:(ESP)
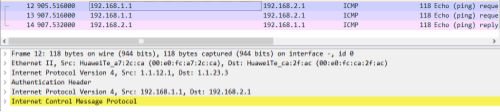
验证:(AH)
[AR1-ipsec-proposal-wolf]dis this
[V200R003C00]
#
ipsec proposal wolf
transform ah
[AR3-ipsec-proposal-wolf]dis this
[V200R003C00]
#
ipsec proposal wolf
transform ah
[AR1-ipsec-policy-manual-wolf-10]dis this
[V200R003C00]
#
ipsec policy wolf 10 manual
security acl 3000
proposal wolf
tunnel local 1.1.12.1
tunnel remote 1.1.23.3
sa spi inbound ah 1234
sa string-key inbound ah simple huawei
sa spi outbound ah 4321
sa string-key outbound ah simple huawei
[AR3-ipsec-policy-manual-wolf-10]dis this
[V200R003C00]
#
ipsec policy wolf 10 manual
security acl 3000
proposal wolf
tunnel local 1.1.23.3
tunnel remote 1.1.12.1
sa spi inbound ah 4321
sa string-key inbound ah simple huawei
sa spi outbound ah 1234
sa string-key outbound ah simple huawei
问题:因为AH针对数据包不加密,那AH有什么用呢?
如果收到的数据包就是加密后的数据包,那此时就可以用AH节约设备资源;
华为认证HCIE培训-IPSEC VPN的模式:
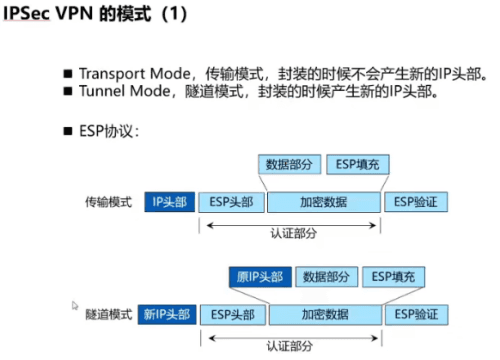
Transport Mode(传输模式):封装的时候不会产生新的IP头部;
就是针对本身的数据ICMP REQUEST进行加密,将加密后的数据加上数据包自身的网络层头部
场景:如果业务地址和IPSEC隧道的SIP和DIP一样时,就可以采用传输模式,节约资源;
Tunnel Mode(隧道模式):封装的时候产生新的IP头部;(默认)
就是针对本身的数据ICMP REQUEST+网络层头部加密,将加密后的数据加上IPSEC VPN的source和des
场景:如果业务地址和IPSEC隧道的SIP和DIP不一样时,就必须采用隧道模式;
WOLFLAB官方微信:17316362402
WOLFLAB官方QQ:2569790740
华为HCIE Datacom培训课程咨询联系WOLFLAB网络技术实验室
WOLFLAB网络技术实验室-华为授权机构
WOLFLAB实验室(华为授权合作伙伴)HCIE讲师:崔志鹏