
News
发布日期:2023-07-28 浏览次数:2393 来源:WOLF-LAB
CCDE笔试400-007只考选择题和拖图题吗?
CCDE笔试400-007目前只考选择题和拖图题,WOLF-LAB实验室CCDE笔试400-007稳定过人中,近期需要备考的同学可以联系客服咨询题库是否稳定。
WOLFLAB官方微信:17316362402
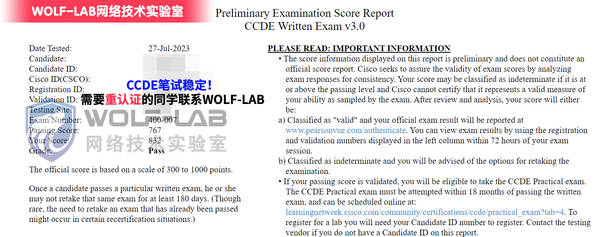
下面分享一些考试题型给大家参考:
1-Which development model is closely associated with Agile project management?与222题相似
A. static model
B. starfish model
C. evolutionary delivery model
✓D. lifecycle model
2-what is a disadvantage of the traditional three-tier architecture model when east west traffic between different pods must go through the distribution and core layers?与139相似
A. low bandwidth
B. security
C. scalability
✓D. high latency
3- According to the CIA triad principles for network security design, which principle should be priority for a Zero Trust network?
✓A. requirement for data-in-motion encryption and 2FA authentication
B. requirement for data-at-rest encryption for user identification within the VPN termination hardware
C. categorization of systems, data , and enterprise BYOD assets that are connected to network zones based on individual privacy needs.
D. Ensuring that authorized users have high-availability system access from defined zones to defined systems or ones.
4- In search of a system capable of hosting , monitoring compiling. and testing code in an automated way , what can be recommended to the organization?
✓A. Jenkins
B. Ansible
C. Perl
D. Chef
5- which two advantages of using DWDM over traditional optical networks are true? (choose two)
A. Inherent topology flexibility and service protection provided without penalty through
Intelligent oversubscription of bandwidth reservation
✓B. ability to expand bandwidth over existing optical Infrastructure.
✓C. inherent topology flexibility with built-in service protection
D. inherent topology flexibility with intelligent chromatic dispersion
E. inherent topology flexibility with a service protection provided through a direct integration with an upper layer protocol.
6- Which two statements describe the usage of the IS-IS overload bit technique? (choose tow)
✓A. If overload-bit is set on a Level 2 intermediate system, the other Level 2 intermediate systems in the topology will stop using the overloaded IS to froward Level 2 traffic However, the intermediate system can still forward Level 1 traffic
B. It can be set in intermediate systems(IS-IS routers) to prioritize control plane CSNP packets.
C. It can be used to automatically synchronize the link-state database between Level 1 intermediate systems.
✓D. It can be set in intermediate systems (IS-IS routers) to avoid traffic black holes until routing protocols are fully converged after a reload operation.
E. It can be set in intermediate systems (IS-IS routers) to attract transit traffic from other intermediate systems.
完整CCDE笔试400-007考试咨询WOLF-LAB网络技术实验室
WOLFLAB官方微信:17316362402
WOLFLAB官方QQ:2569790740